Team
- Ryan A Balloun
- George Cusack
- William E Leyman
- Harrison W Waxler
Mentors
J. Mottley & D. Phinney
Abstract
Communications over a mobile phone network, while encrypted, are not difficult to eavesdrop on by a dedicated attacker. To prevent unauthorized parties from listening to a private conversation between two users over the phone, we propose an encrypted two-way “texting” interface that sends data over a phone line using our device. Two users are able to type out and receive messages from each other on a computer with minimal chance of incorrect or lost data experienced by the other side.
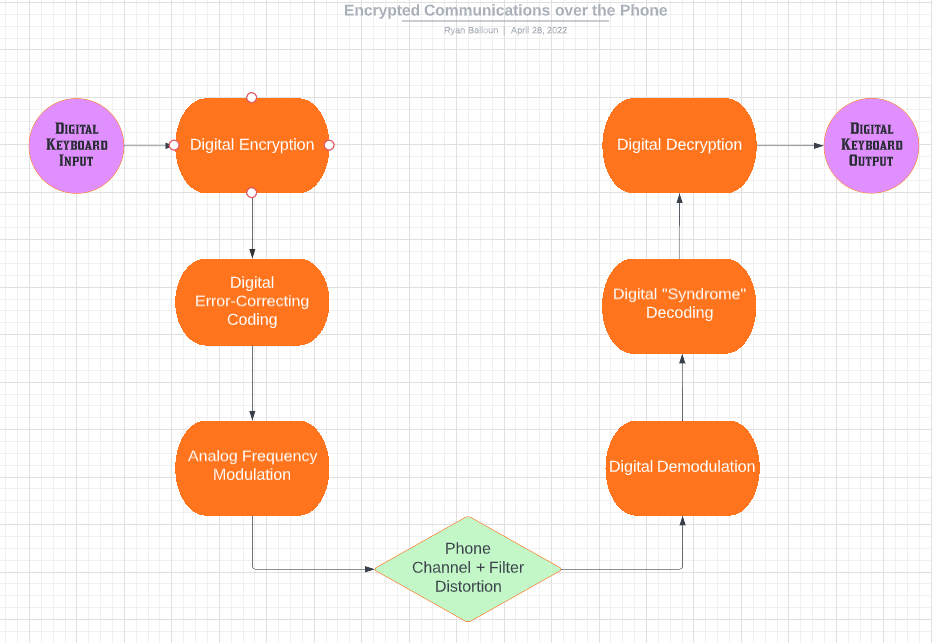
Design Block Diagram
Physical Circuit!
Diving into the Details
Our design relied on the Teensy 4.0 microcontroller to do much of the heavy lifting for the encryption and error-correction coding on the text message being sent. Each of the three main parts of our project (encrypting, coding, and modulating) involved technologies we were taught throughout classes in the undergraduate curriculum. These technologies are discussed more below.
Encryption/Decryption
We attempted both AES and RSA encryption, but encountered issues with added bit overhead. Each algorithm added additional bytes to the source text for a 1:4 and 1:2 ratio of source text to cipher text. This negatively affected the amount of data we were able to send over the phone at a time.
Our team ultimately chose to use RSA for the encryption of our messages between the paired devices. RSA offers a concrete advantage over other common, secure encryption algorithms such as AES in that it is a public-key algorithm. This means that RSA is able to support more users because it’s easier to make connections between new pairs of users without comprising the security of each user. The downside of RSA is that it takes longer to encrypt data than AES.
Coding / Decoding
There’s no guarantee that data will make it over a phone line unaltered, and we experienced an issue with Bit Error Rate (BER) over the course of a text conversation. To remedy this, we used a Hamming Error-Correcting Code (ECC) that added some redundant bits to our data. This [7 4] Hamming Code was capable of correcting some of the corrupted data bits on the receiver end, making the issue of retransmitting a failed message far less likely.
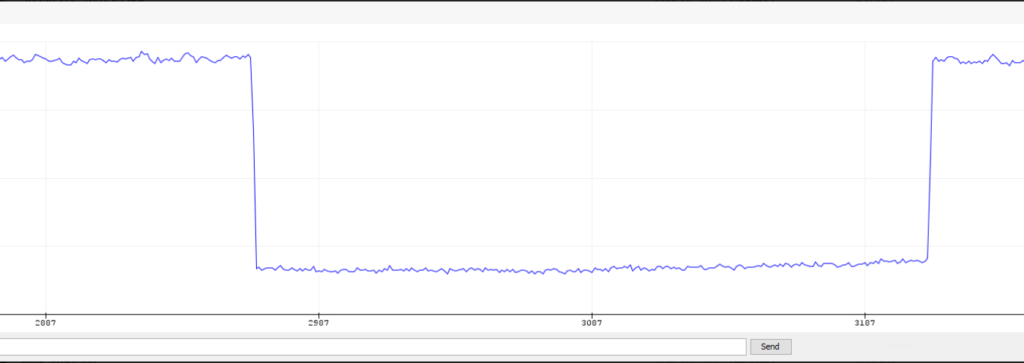
Modulation/Demodulation
In order to send bits over the phone jack to be transmitted to a receiver phone, bits must be represented as a voltage-controlled analog signal over a wire instead of staying in the digital memory of the Teensy. More specifically, ‘0’s and ‘1’s are sent using different analog voltage frequencies on the wire. Our prediction was that the frequency of the transmitted message was the most likely thing to survive the journey between transmitter and receiver, as opposed to the amplitude or phase of the wave. This kind of modulation is known as Binary Frequency-Shift Keying (B-FSK). Given the difficulty of synchronizing the transmitter and receiver and properly demodulating the bits, we only had time to test B-FSK and not other modulation algorithms.
We created a perfboard design with all the necessary components for a simple interface to modulate bits coming from the Teensy 4.0 to B-FSK format.


