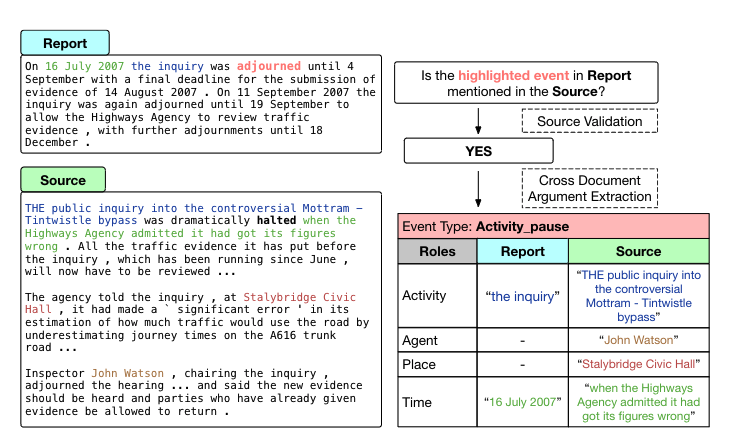
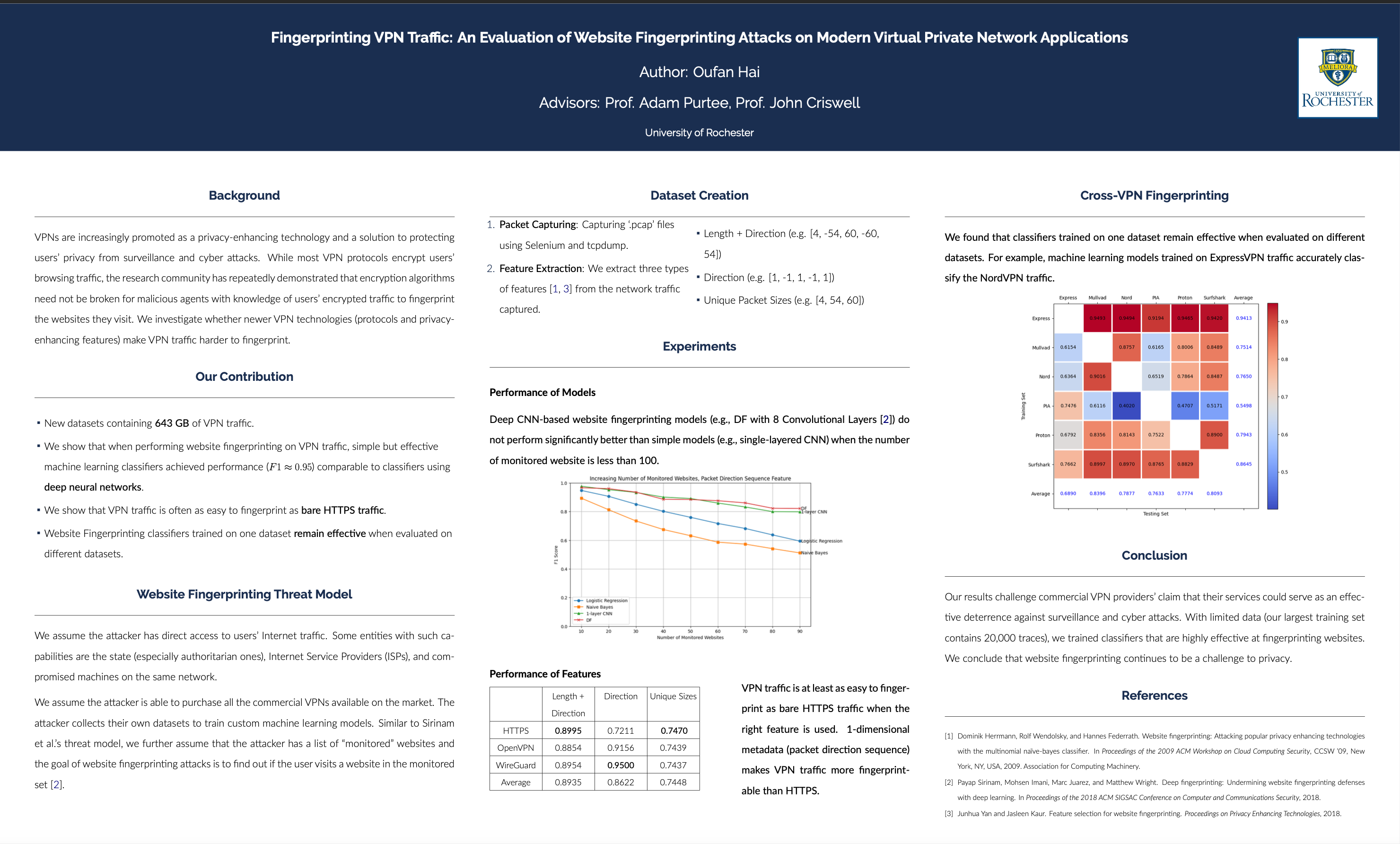
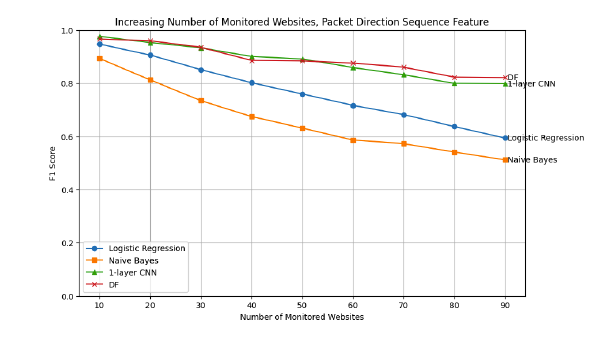
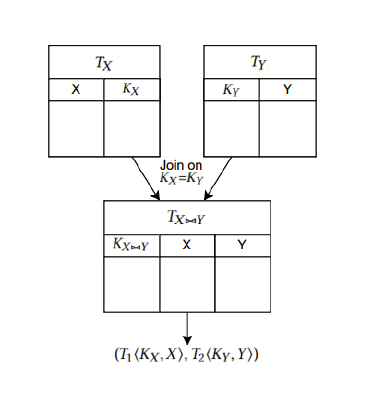
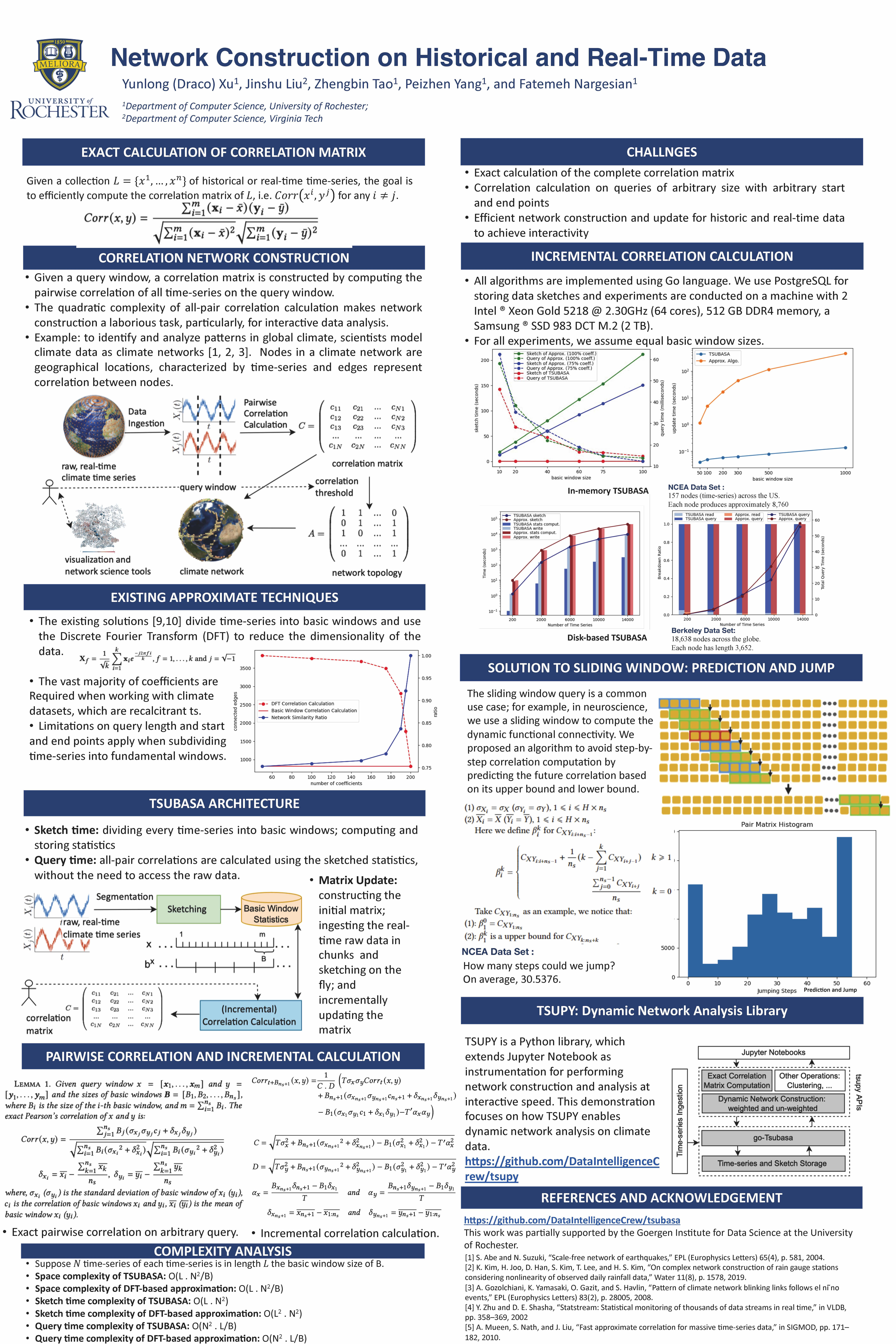
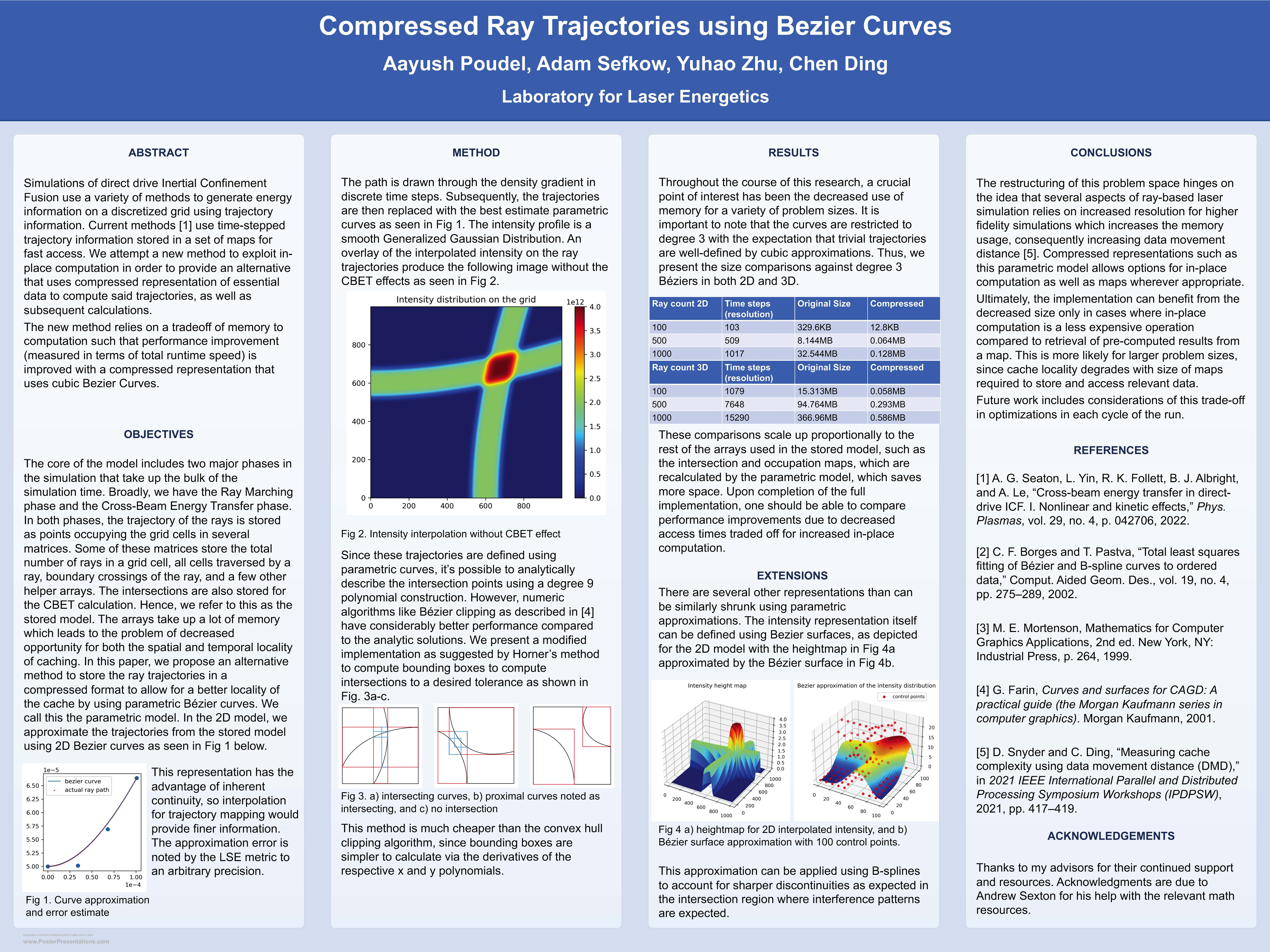
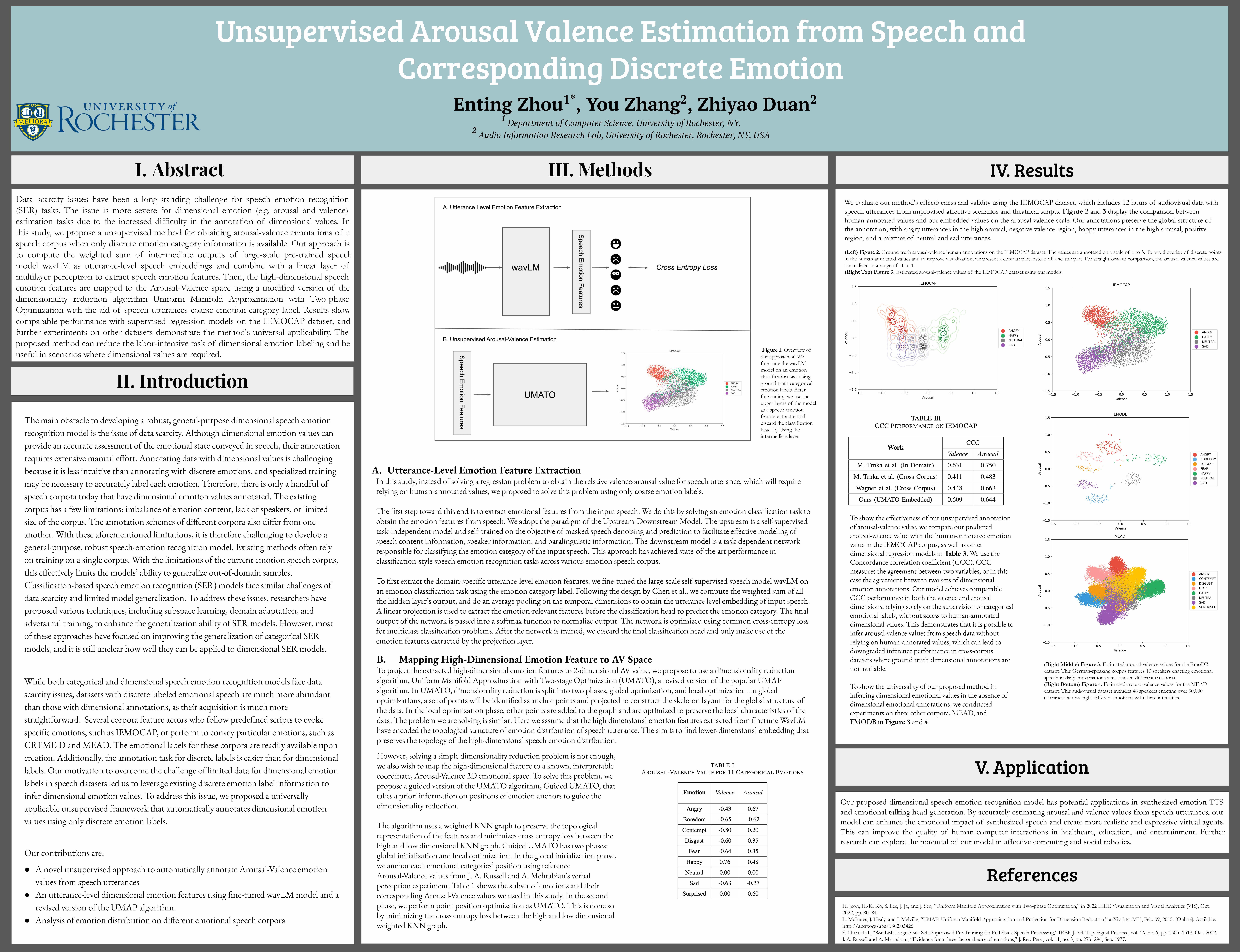
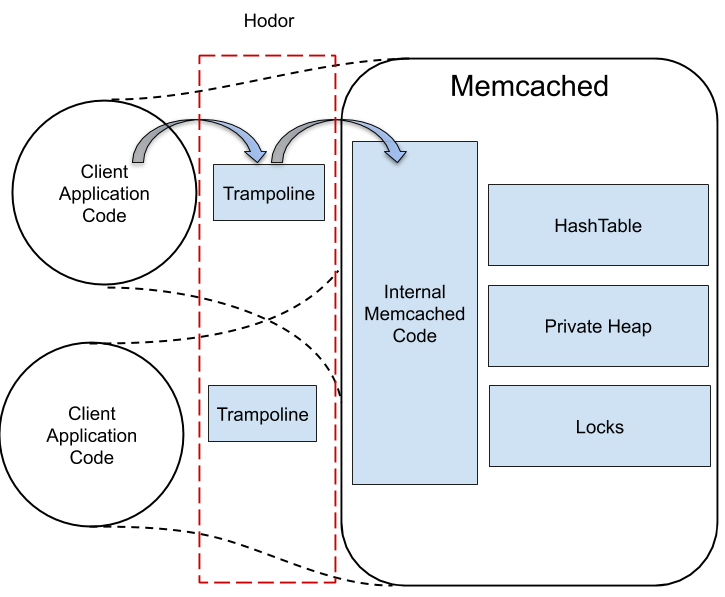
Memcached is a widely used key-value (KV) store. It is structured
as a multithreaded user-level server, accessed over socket
connections by a potentially distributed collection of clients.
Because socket communication is so much more expensive
than a single operation on a KV store, much of the client
library is devoted to batching of requests. Batching is not
always feasible, however, and the cost of communication
seems particularly unfortunate when—as is often the case—
clients are co-located on a single machine with the server,
and have access to the same physical memory.
Fortunately, recent work on protected libraries has shown
that it is possible, on current Intel processors, to amplify access
rights quickly when calling into a specially configured
user-level library. Library instances in separate processes
can then share data safely, even in the face of independent
process failures. We have used protected libraries to implement
a new version of memcached in which client threads
execute the code of the server themselves, without the need
to send messages. Compared to the original, our new version
is both significantly simpler, containing 24% less code, and
dramatically faster, with a 11–56× reduction in latency and
a roughly 2× increase in throughput.