3. Programs Archive
Fingerprinting VPN Traffic: An Evaluation of Website Fingerprinting Attacks on Modern Virtual Private Network Applications
April 23, 2024
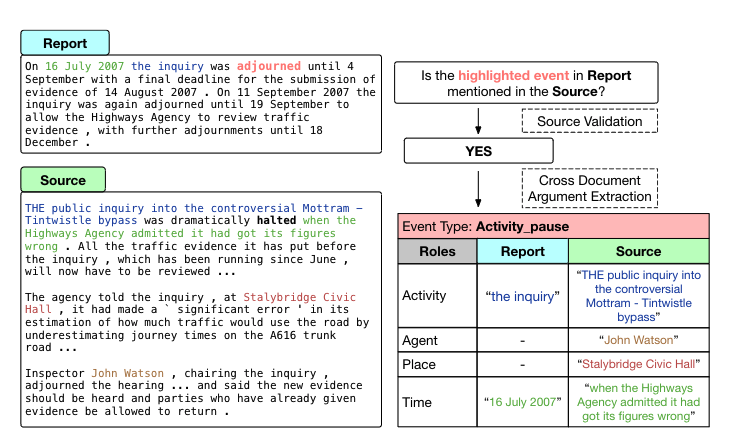
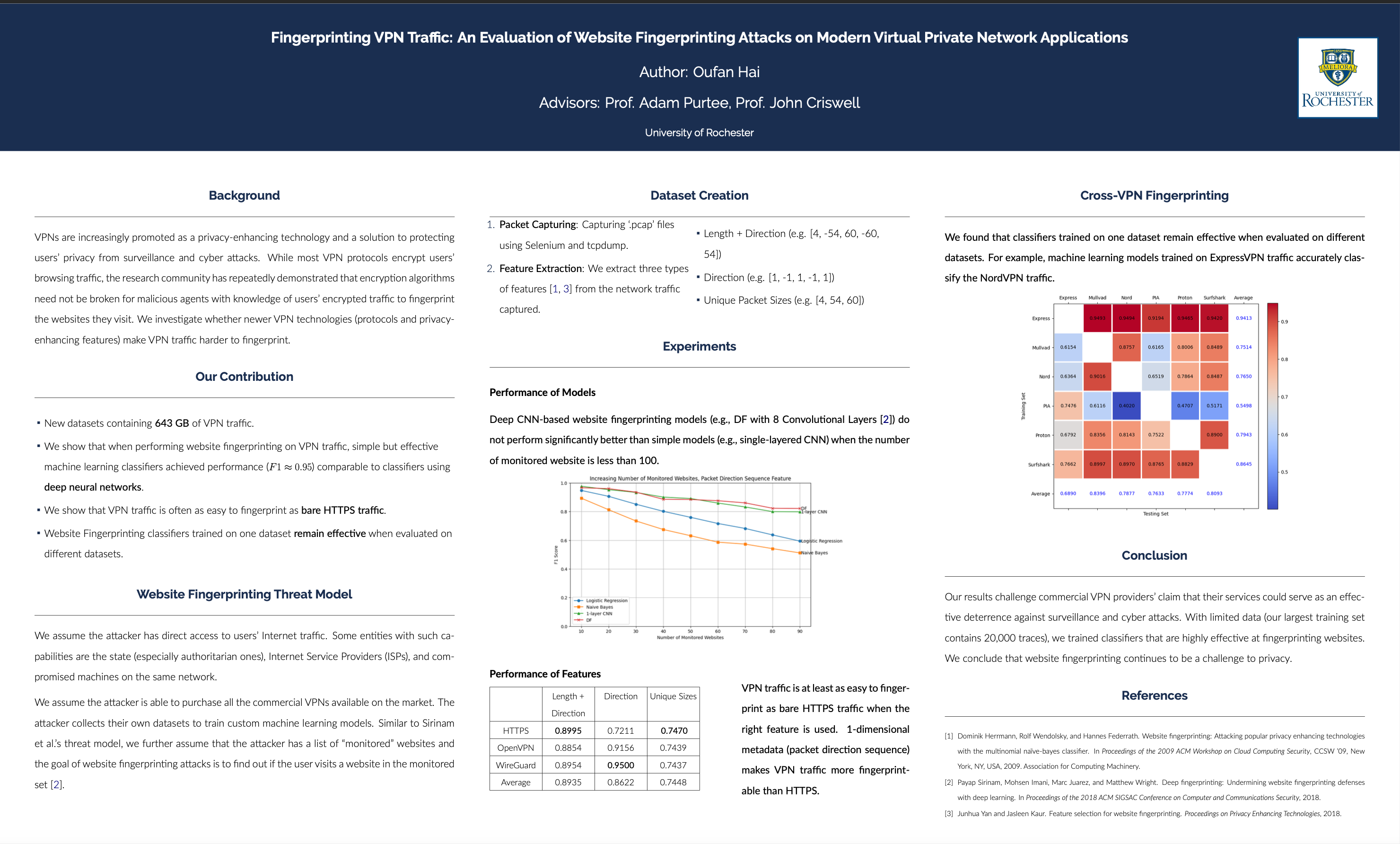
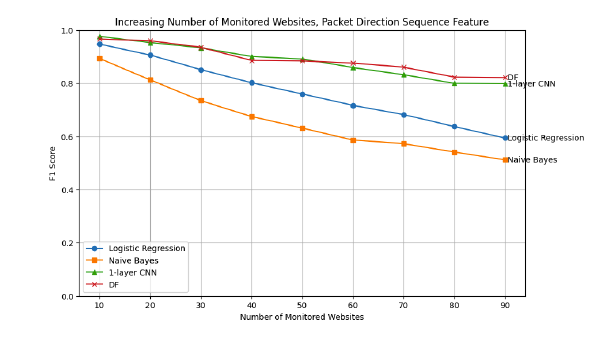
VPNs are increasingly promoted as a privacy-enhancing technology and a solution to protecting users’ privacy from surveillance and cyber attacks.1 While most VPN protocols encrypt users’ browsing traffic, the research community has repeatedly demonstrated that encryption algorithms need not be broken for malicious agents with knowledge of users’ encrypted traffic to fingerprint the websites they visit. We investigate whether advancements in VPN technologies in the last two decades make VPNs harder to fingerprint.